Step 1. Generate CycloneDX SBOMs
Where to start?
The first decision to take is - how and when is the SBOM file created. Of course, this also depends on where you stand in regard to the creation of SBOMs. There are multiple ways you might be creating SBOMs already, but the tool needs to generate the SBOM automatically as close as possible to the build of the software artifact. This is also clear guidance by the NTIA.
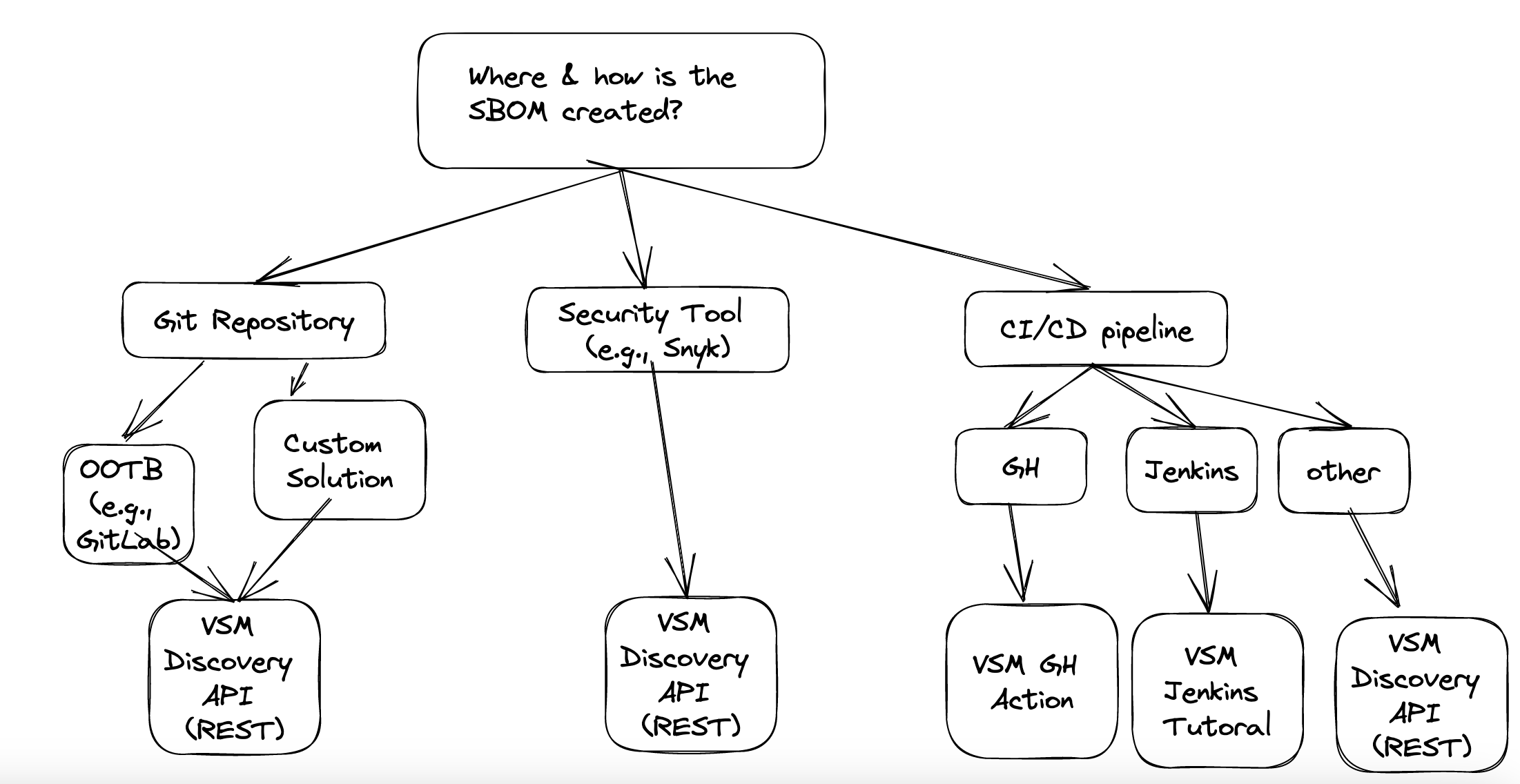
As outlined above we fundamentally see 3 different options:
- Right from the Git Repo
- From a security Tool
- From your CI/CD Pipeline
TL;DR
If you dont have any existing SBOM generation setup, we recommend to deploy our open-source prototype (scenario 1 - option 2.2). While experimental, it will help you to generate SBOMs fast and show the value of VSM to your organization. This will also help you to approach your development teams for which the tool is not able to produce an SBOM to use the CI/CD plugin approach .
Also it is perfectly possible to run the
vsm-sbom-boosteron a schedule to ensure up-to-date SBOMs.
Scenario 1: Right from the Git Repo
Option 1: Your Git Provider supports SBOM OOTB
In this case, you simply need to generate the SBOM from your native Git provider tooling (e.g., GitLab), and send it to LeanIX VSM's Discovery API.
Option 2: Using a custom solution to generate SBOMs for all your repositories
In case your Git Provider cannot natively create SBOMs, you can also use open-source operated on your side to
- access all code repositories
- use our open-sourced prototype to centrally generate SBOMs. Feel free to reach out to your CSE to discuss the options to deploy this on your estate.
VSM SBOM Booster - Open source SBOM generation tool
We have open-sourced a SBOM generation tool that can crawl your Git repositories, generate the SBOM and provide it to VSM as a central mechanism to generate the SBOMs. It leverages the ORT (a powerful open source SBOM generation tool) to do its job. We are happy for any contributions to extend it's functionality.
Please find the details here.
- send the resulting file to LeanIX VSM's Discovery API
Outlook
If you are interested in this option, please let us know - we plan to make it easier for you to implement this this approach by providing a tutorial and example code.
Scenario 2: Using a security tool
Similar to the Git Provider case above, in this case you can simply consume the SBOM provided by the respective security tool, and sent it to the VSM Discovery API.
There is a growing number of software security providers that can generate CycloneDX SBOMs as part of their screening already. To name a few: snyk, Jfrog Xray, sonatype.
These mostly - at the point of writing - are also young product offerings that will see some maturity in their quality. In any case, you can write a simple middleware solution to regularly send the SBOMs via our REST API into VSM.
Scenario 3: As part of your CI/CD pipeline
Recommendation
If you chose this approach we also recommend to set up schedule-based triggers for the pipeline, to ensure that fresh SBOMs are available for all your services - not only for those that are seeing other code changes. Reasoning: the most dangerous services you have are those that you do not deploy regularly as their dependencies will age automatically.
Step 1: Embed the CycloneDX SBOM generation as part of your build process
Best Practice - CycloneDX SBOM generation
We strongly suggest using the SBOM plugins provided by the CycloneDX initiative for the combined use with VSM. For the main package managers, these plugins are easy to embed and reliably extract all relevant information (dependency tree incl. transitive dependencies, consistent use of the PURL and licenses) from your build files.
Please navigate to our guide on how to embed the CycloneDX plugins for the main package managers in your build process:
Step 2: Provide the SBOM file to VSM (as part of your build)
Create a step in your CI/CD pipeline to provide the CycloneDX SBOM file on a continuous basis to VSM. This is a one-time setup.
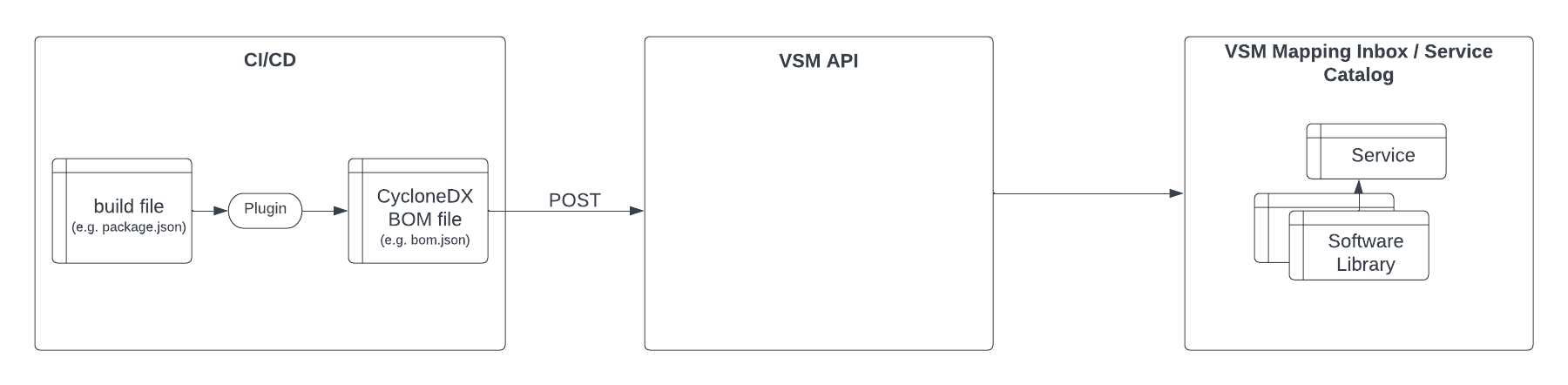
CI/CD setup
See the details in the technical setup guide:
Example: Utilise CI/CD wrappers
Refer to this tutorial for a sample setup with Jenkins:
or check out the curated VSM GitHub action: https://github.com/leanix/vsm-discovery-github-action
This is a lot of work.
At this point you're absolutely right. That's why we have open-sourced our prototype to automate and centralize a lot of the heavy-lifting of the SBOM generation (see project here), as we internally saw those large overheads as well. While we believe tools like this help, they are only a bandaid for the real solution.
We firmly believe that in the mid- to long-term SBOM generation should not be developer work at all.
Our expectation is that tooling should fully & reliably (see SBOM quality) automate this. Today, tooling is still requires maturing. Hence, we looked for options today and found a promising one.
A note on SBOM quality
There is an evergrowing number of SBOM generation tools, but the quality of the SBOM varies significantly as tooling needs to mature both in automation and reliability. Read our blog article to get a taste of the current state of affairs. The NTIA also stipulates minimum requirements for SBOMs provided to US government agencies as part of the executive order 14028.
As a yardstick, your SBOM and VSM shine when:
- the SBOM contains valid PURLs
- the SBOM has a valid license for all its PURLs
- the SBOM entails all (transitive + direct) libraries
There are a set of open-source tools that can measure SBOM quality. These might help as auxiliary services to ensure high SBOM quality. Find a curated list below:
Updated 10 months ago

