VSM Vision
Find out where the VSM product is heading
This page provides a write-up of the VSM vision. It shall not be confused with a firm roadmap but rather serves as a compass and shows where the VSM product is heading to.
Vision
We want to be the go-to product for product development teams that use secure technology to build valuable products. Like a Google Maps for development organizations.
Mission
We do so by discovering your self-built software. This data is then put in the context of ownership of your development organization, is available for government processes, and is aggregated to the products you are building. With VSM in place, you can focus on efficiently and securely delivering value with your products while we help you to level up your development organization.
Let's hear from our CTO - Steffen Wittmann

"Before adopting VSM internally, LeanIX was facing the same challenge as many of our customers: data relevant for the engineering teams, myself, and my stakeholders was locked away in disconnected silos - our vulnerabilities in Snyk, our Code Repositories in GitHub, our Teams on a poorly maintained Confluence page, and most but not all of our APIs in an internal SwaggerHub. Only a few experts could tell me what was really running in our Kubernetes clusters and in Azure. These circumstances made it extremely hard to stay on top of risks and effectively deploy my budget to achieve our business goals. And each time a new exploit trended on Twitter I got nervous and asked my direct reports to double-check if we were affected as well.”
The IT landscape is changing and two trends are emerging more than ever: SaaS and self-built software. Most applications on the landscape will fall into one of these two categories rather sooner than later. As a consequence technology organizations of tomorrow need to master the craft of building valuable software products, that drive their business goals. However, self-built software products and their maintenance bring a bunch of challenges, such as security, stability, and architectural complexity that IT organizations need to be on top of. By being the Google Maps for software, VSM provides peace of mind that the risks of modern software development in your organization are being addressed so that you can focus on delivering value with your product.
Service catalog and team ownership are a necessary foundation for your organization
"...data relevant for the engineering teams, myself, and my stakeholders was locked away in disconnected silos... - Steffen Wittmann, CTO@LeanIX
The absence of overview and ownership in your organization creates significant challenges that hinder your efficiency and ability to provide high-quality services to your customers. The lack of clarity and visibility regarding available services leads to confusion and delays in service delivery. A lack of clear responsibilities results in overlapping efforts and an inefficient resource allocation. The inconsistent service quality across teams and departments damages your reputation and customer trust. Without a structured foundation, scaling operations and introducing new services and products becomes difficult.
Finally, the lack of collaboration and knowledge sharing among teams creates silos and impedes problem-solving. To overcome these obstacles, implementing a service catalog and promoting team ownership is crucial to enhance your operational efficiency, service consistency, scalability, and collaboration within the organization.
Get a 360° view of your services based on automatic data discovery
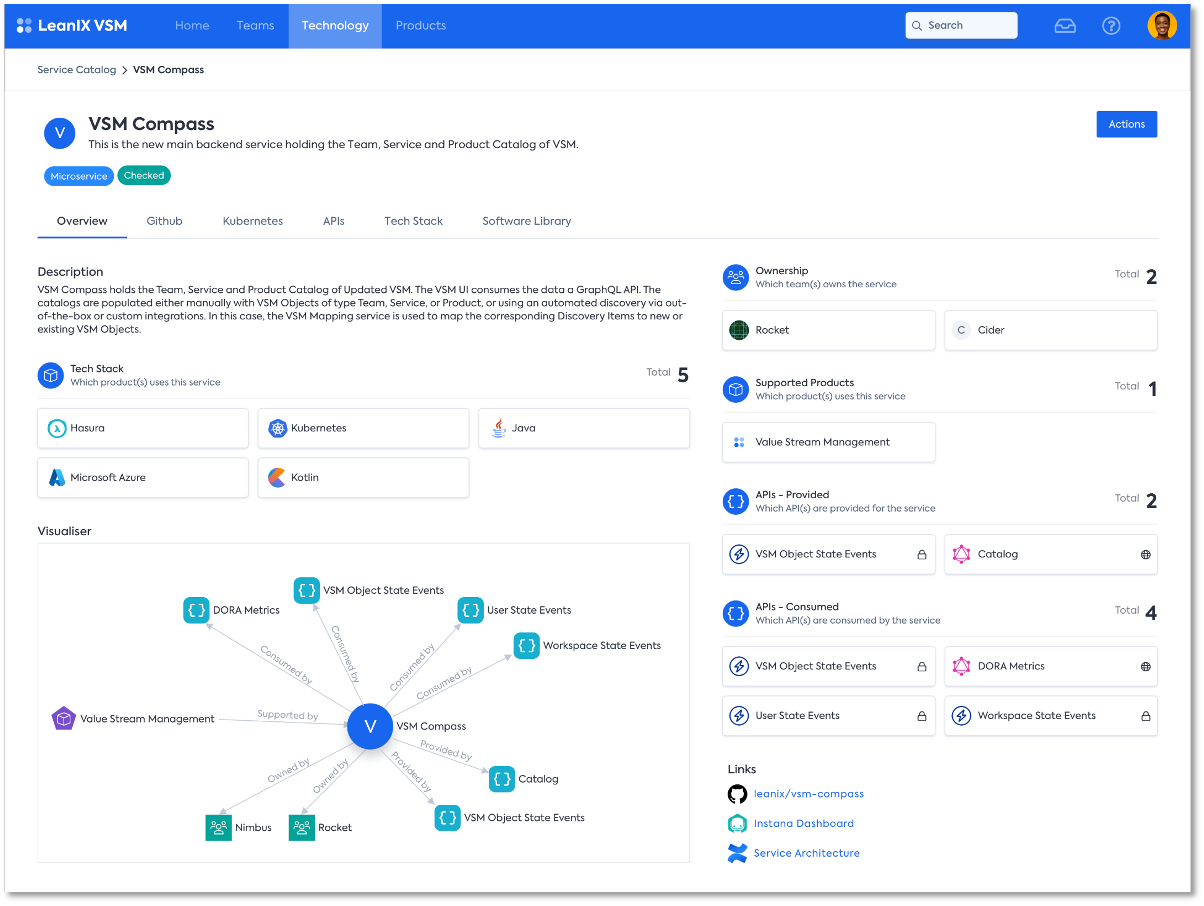
The Service page is at the core of VSM
To navigate the complexities every product development organization faces, automated transparency about the existing assets, their ownership, and their status is crucial. Can I use a specific API for the new service my team is working on, even if we will be adding a lot of load? Whom to talk to before changing the contract of an API? Is the expertise in our teams aligned with the needs of our business - or do I need to accelerate the hiring of frontend engineers in a specific business unit?
The Service Catalog is powered by seamless integrations into all big git repository providers: GitHub, GitLab, Bitbucket, and Azure Repositories.
Deliver curated insights to your teams that power security and efficiency
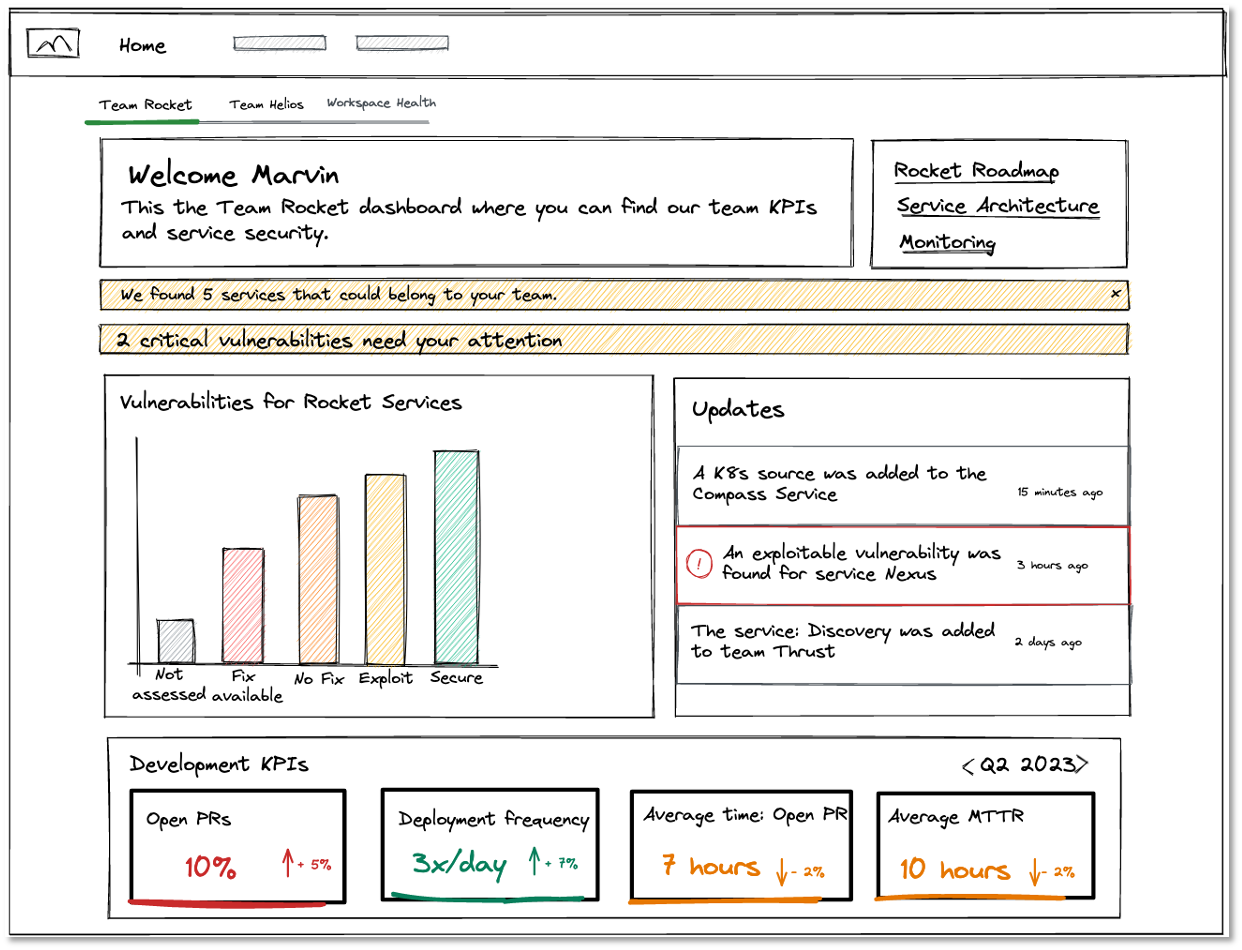
The team dashboard becomes the central aggregation of information relevant to each development team. Keep informed about the latest changes in the catalogs. Actionable insights based on open-source risk and data quality are provided to the team. Development KPIs allow the team to self-reflect and identify room for improvement.
The essence of your engineering organization on tailored management dashboards
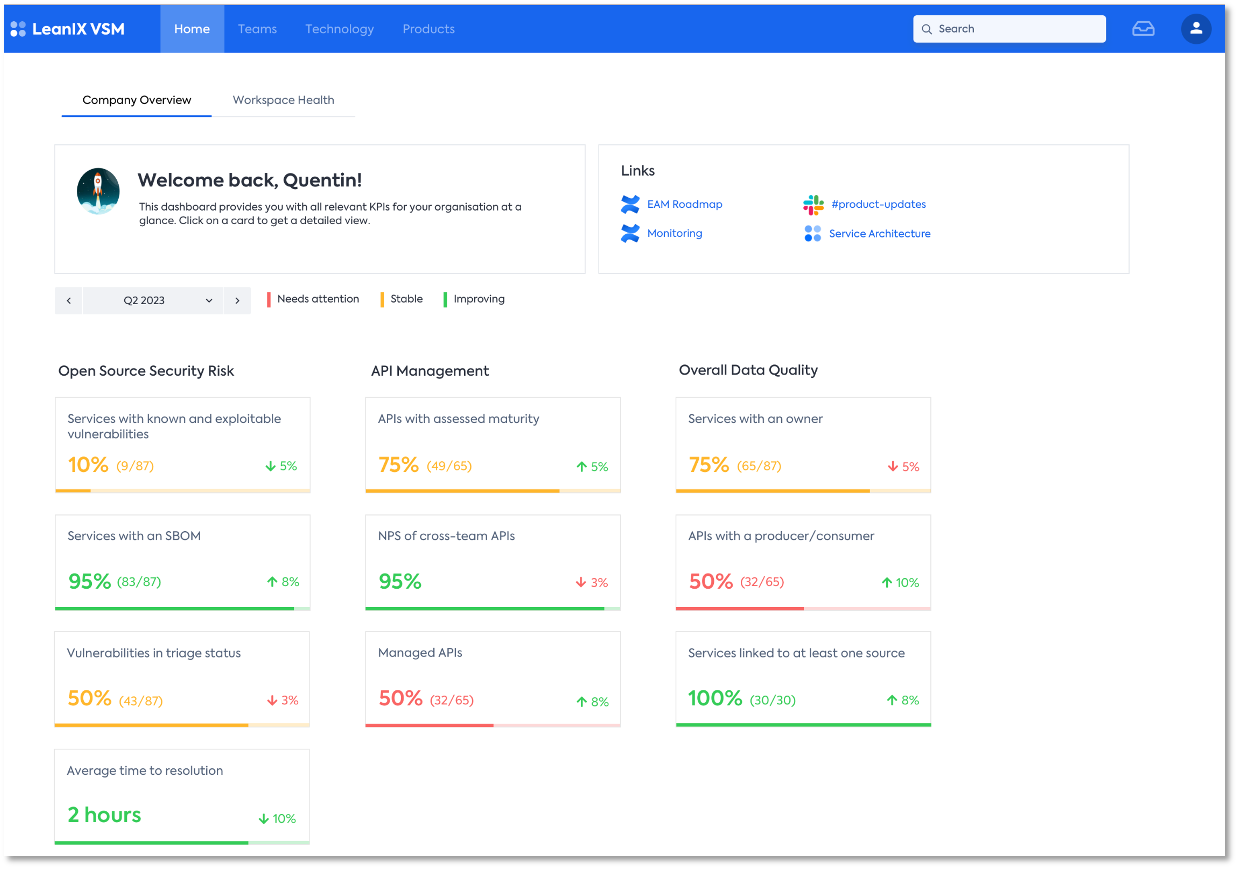
Our dashboards provide peace of mind to engineering leaders by offering tailored views for different parts of your organization. They aggregate open-source software risk data, providing a comprehensive understanding of potential vulnerabilities. Additionally, our dashboards offer an API and service management overview, allowing for efficient decision-making and proactive monitoring. With these features, engineering leaders can confidently navigate software development, optimize performance, and prioritize security efforts effectively.
Understand complexities and inter-service dependencies
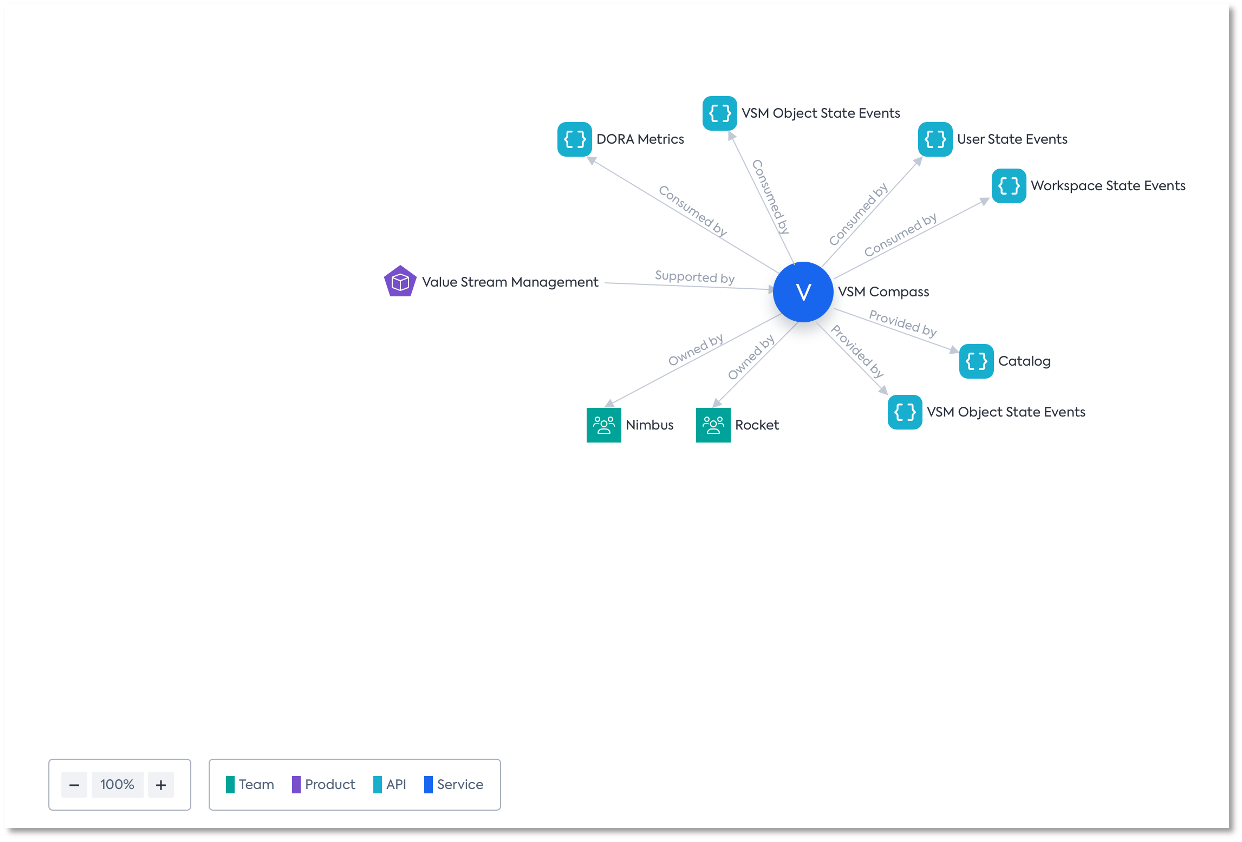
Based on the discovered data, anybody can - visually and highly interactive! - explore the resulting connections between the teams, the services & APIs they own, and the products they support. With this foundation, we democratize knowledge to foster easy access to information and inform management of the different concerns in a development organization.
Getting open source software risk under control is essential for building secure software
"And each time a new exploit trended on Twitter I got nervous and asked my direct reports to double-check if we were affected as well.” - Steffen Wittmann, CTO@LeanIX
Open-source components are widely adopted in software development due to their cost-effectiveness, flexibility, and collaborative nature. However, the increasing reliance on open-source software introduces inherent vulnerabilities and potential security threats that must be effectively mitigated. Currently, organizations struggle to maintain control over open source software risks, leading to compromised software security and exposing users to various cyber threats. Therefore, there is an urgent need to address the challenge of getting open source software risk under control to ensure the construction of secure software systems and safeguard the integrity, confidentiality, and availability of sensitive data.
VSM's three-pronged approach to leverage SBOMs to hand Open Source risk at scale
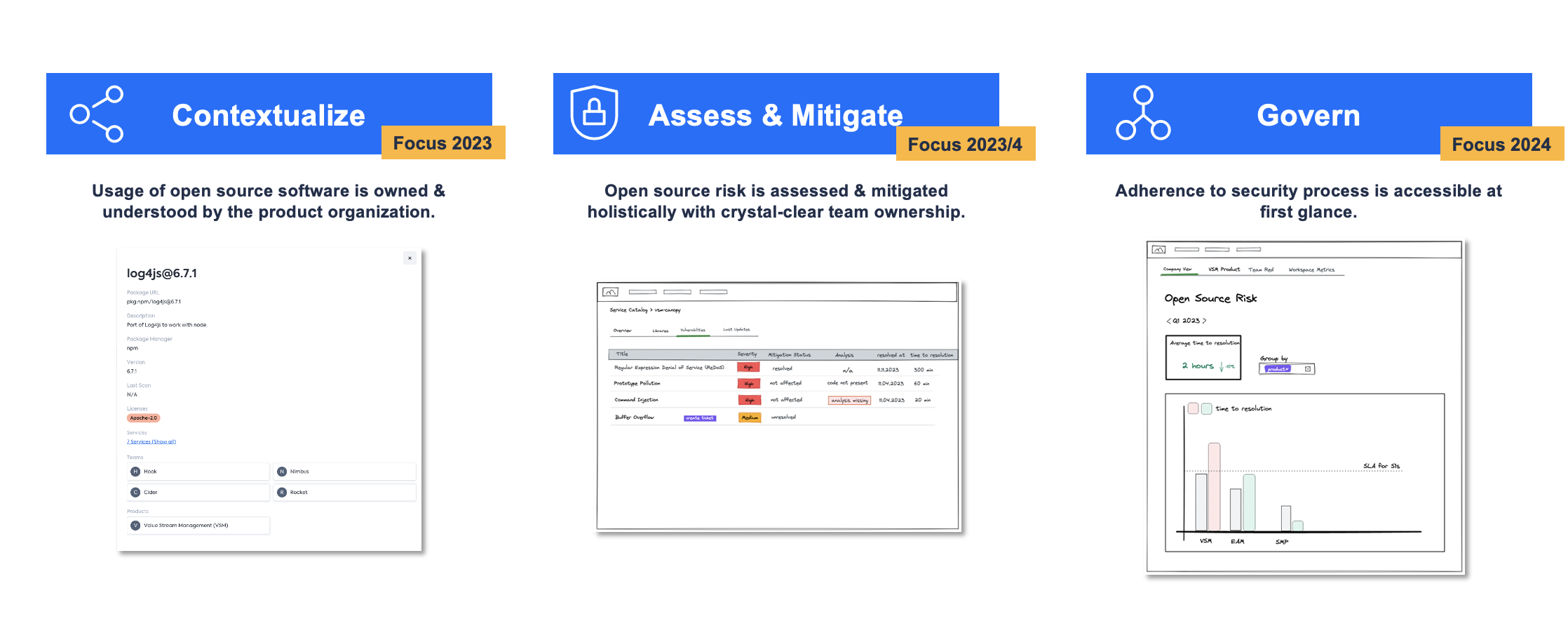
VSM adopts a three-pronged approach to leverage Software Bill of Materials (SBOMs) for effective management of open source software risk. Firstly, VSM focuses on contextualizing open-source software usage within the product organization, ensuring a clear understanding of its ownership and usage. This enables the organization to manage better and control open-source components. Secondly, VSM emphasizes holistic management & mitigation of open source software risk, with well-defined team ownership. This approach facilitates proactive identification and mitigation of vulnerabilities, ensuring a more secure software ecosystem. Lastly, VSM helps instill powerful governance workflows to keep the organization safe at every turn, helping teams prioritize immediate reaction and documentation of open-source software incidents, enabling swift mitigation and creating a valuable knowledge base for future reference. By incorporating these three pillars, VSM enables organizations to effectively handle open source software risk and enhance software security.
Generate and share high-quality SBOMs for your products
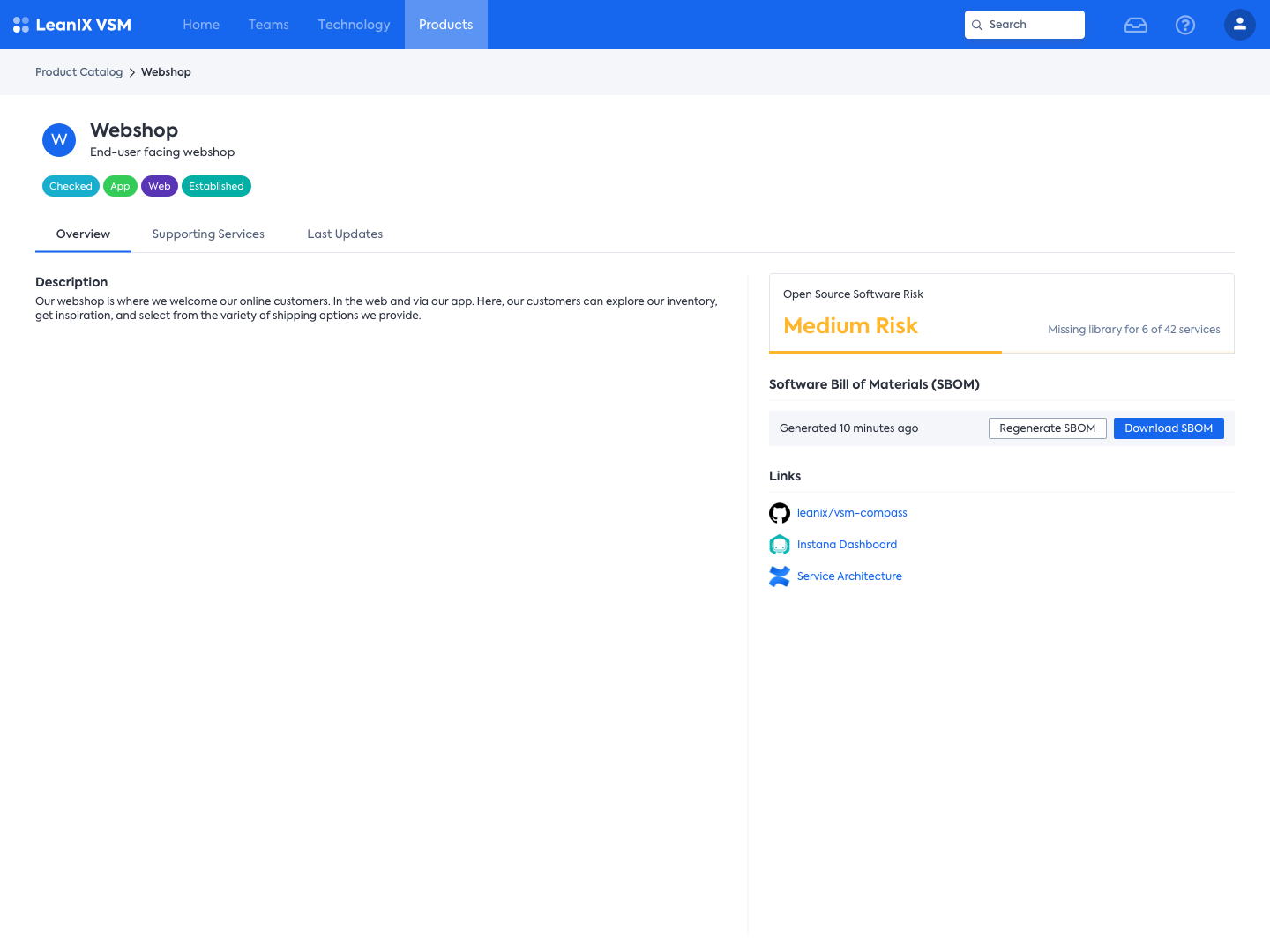
VSM generates accurate product-level SBOMs by leveraging it's knowledge about the composition of products into services, automated processes and integrations with various software development tools. This ensures that the SBOMs are comprehensive and up-to-date, reflecting the open-source components used in the products. We understand the importance of compliance with regulations such as those set by the US government. Therefore, VSM provides mechanisms to assess the quality of the SBOM data, including checking for completeness, accuracy, and consistency. This helps in identifying any gaps or discrepancies in the SBOMs and ensures that the information shared is reliable and trustworthy. It provides features and capabilities to align with these compliance requirements, allowing organizations to confidently meet the necessary standards and regulations. By combining these elements, VSM enables organizations to generate, assess, and share high-quality SBOMs, enhancing transparency and facilitating effective management of open-source components in their products.
Drill into detailed reporting on your libraries to assess and manage risk
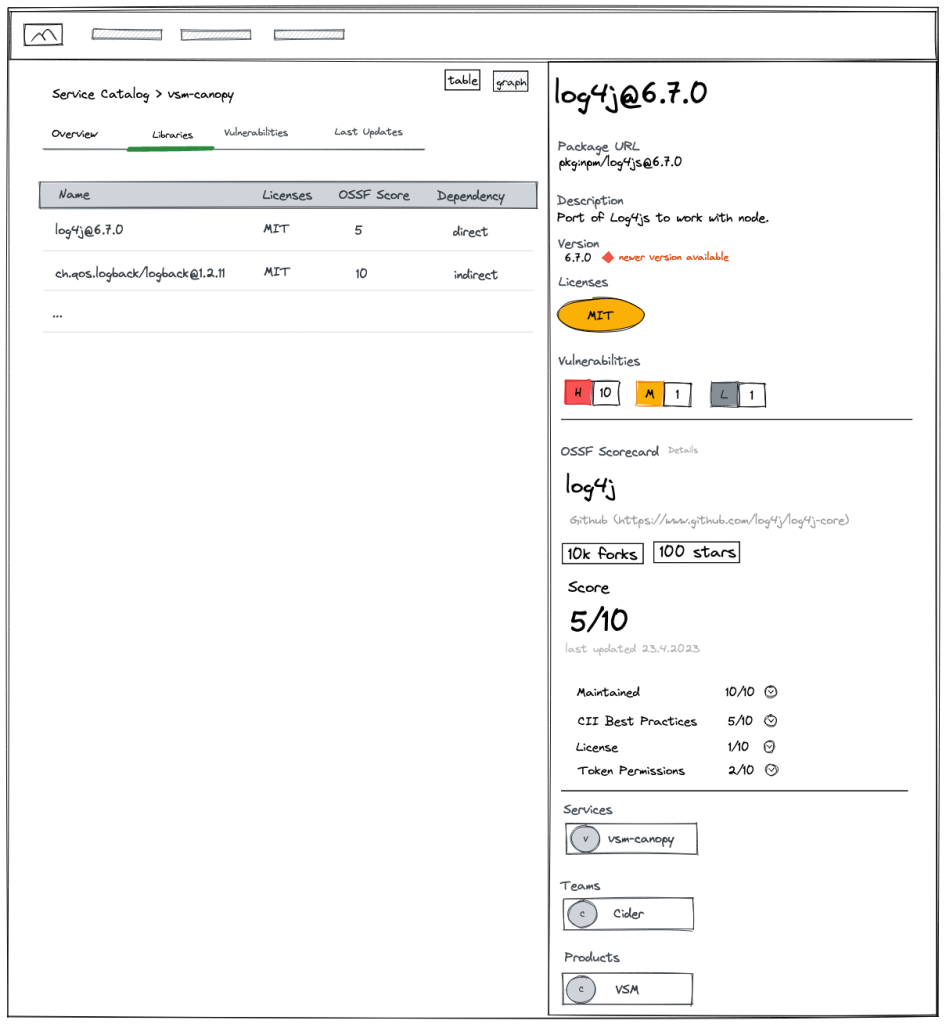
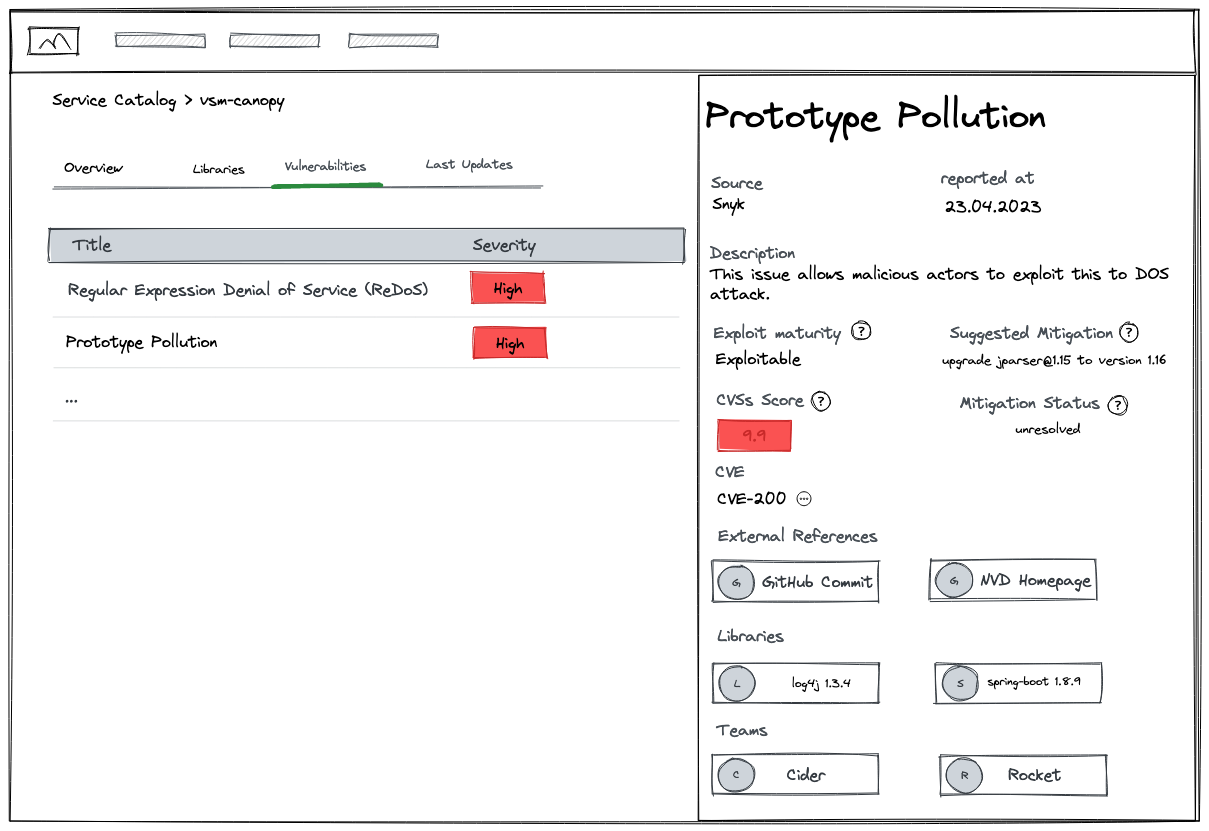
VSM provides a comprehensive set of features to effectively assess and manage risk associated with open-source libraries. With VSM, you can drill into detailed reports on your libraries, gaining insights into potential vulnerabilities and their impact. VSM also incorporates vulnerability scoring, enabling you to prioritize and address high-risk issues promptly. Additionally, VSM offers valuable details on known exploits, empowering your organization to proactively protect against potential attacks. Moreover, VSM provides reference data on affected services and response teams, facilitating collaboration and accountability in addressing vulnerabilities. You can leverage VSM's integration capabilities to access vulnerability data from trusted sources like Sonatype or Snyk, ensuring that you have the most up-to-date and reliable information to inform your risk management efforts. By encompassing these functionalities, VSM equips organizations with the necessary tools to assess, mitigate, and effectively manage open-source softwre risk in their software projects.
Mitigate risk with a guided workflow
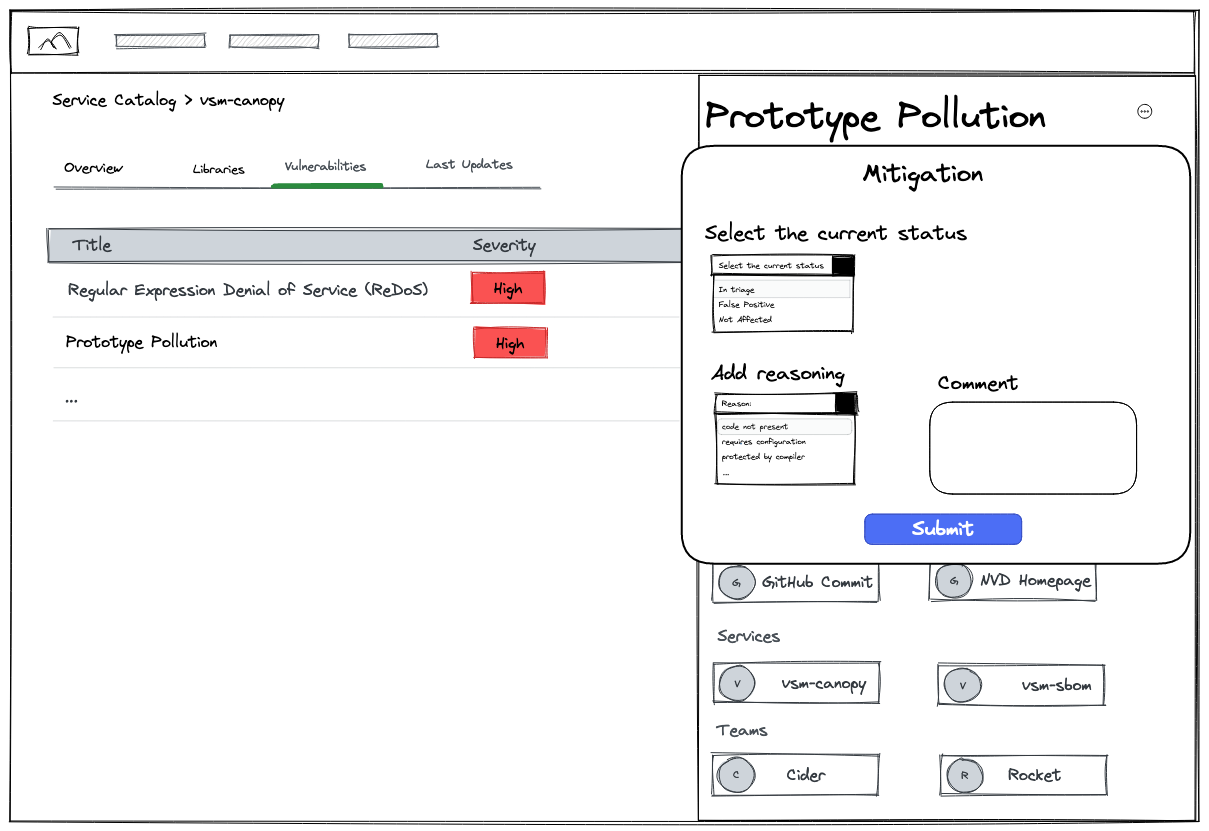 Lastly, VSM offers a curated workflow that helps organizations effectively mitigate risk associated with open-source software vulnerabilities. With VSM, mitigation actions can be triggered automatically, enabling swift responses to identified risks. VSM provides a clear view of services and responsible teams affected by vulnerabilities, promoting transparency and collaboration in the risk mitigation process. Organizations can make informed decisions by assessing the severity of vulnerabilities and either removing them through remediation efforts or accepting them based on risk tolerance. The output of the mitigation will be exportable into industry standards that are compliant with the regulation, such as VEX. By streamlining and automating these risk mitigation procedures, VSM empowers organizations to proactively address vulnerabilities and maintain a secure software ecosystem.
Lastly, VSM offers a curated workflow that helps organizations effectively mitigate risk associated with open-source software vulnerabilities. With VSM, mitigation actions can be triggered automatically, enabling swift responses to identified risks. VSM provides a clear view of services and responsible teams affected by vulnerabilities, promoting transparency and collaboration in the risk mitigation process. Organizations can make informed decisions by assessing the severity of vulnerabilities and either removing them through remediation efforts or accepting them based on risk tolerance. The output of the mitigation will be exportable into industry standards that are compliant with the regulation, such as VEX. By streamlining and automating these risk mitigation procedures, VSM empowers organizations to proactively address vulnerabilities and maintain a secure software ecosystem.
Accurate architecture diagramming is supported by automated API discovery
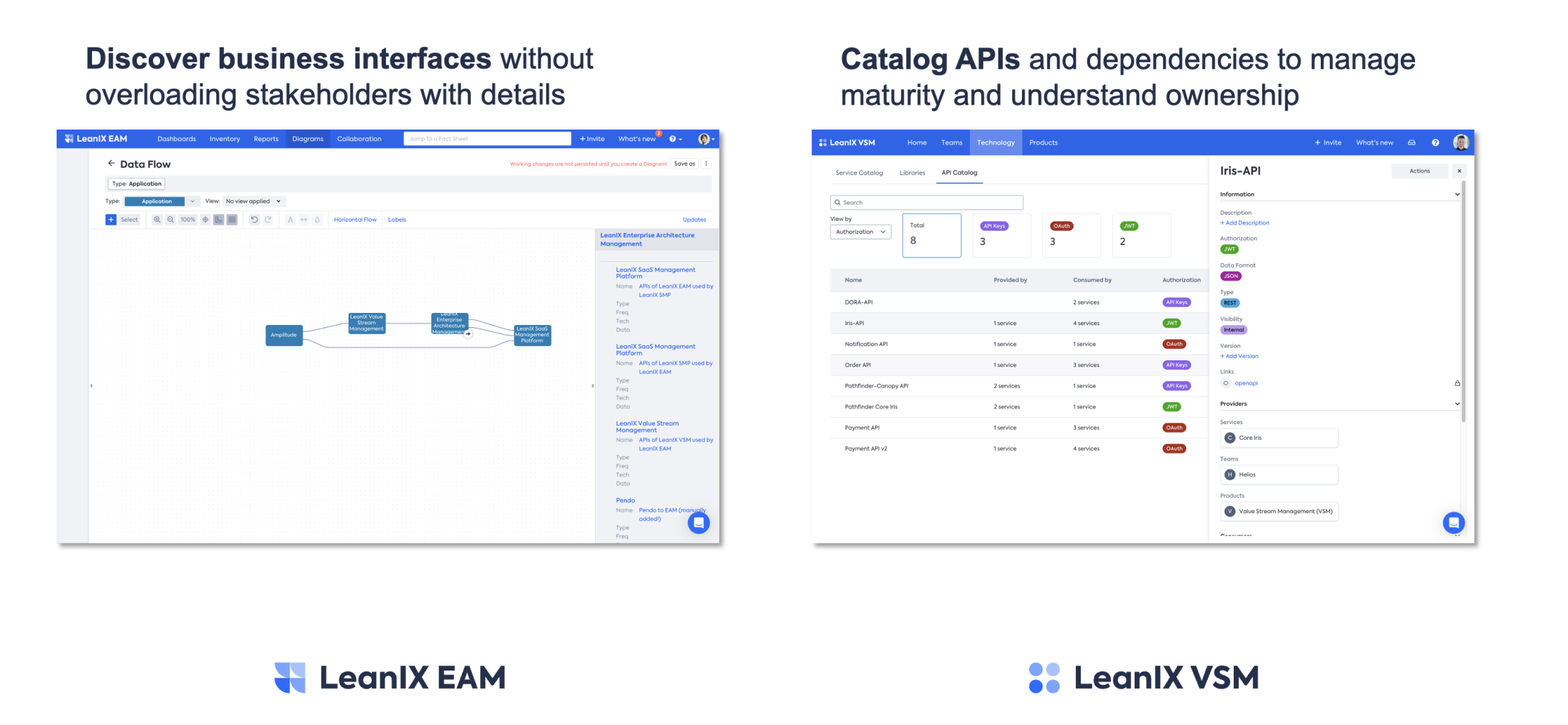 In the realm of EAM, it is crucial to enhance interfaces within the workspace. A valuable strategy involves incorporating automated Application Programming Interface (API) information obtained from the Value Stream Mapping (VSM) process. By leveraging this integration, EAM practitioners can effectively streamline operations and enhance overall efficiency. Moreover, this approach allows for the discovery of business interfaces without burdening stakeholders with excessive details. Through cataloging APIs and their dependencies, organizations can successfully manage the maturity of their systems and gain a comprehensive understanding of ownership. This comprehensive approach empowers EAM teams to make informed decisions, optimize workflows, and achieve successful outcomes.
In the realm of EAM, it is crucial to enhance interfaces within the workspace. A valuable strategy involves incorporating automated Application Programming Interface (API) information obtained from the Value Stream Mapping (VSM) process. By leveraging this integration, EAM practitioners can effectively streamline operations and enhance overall efficiency. Moreover, this approach allows for the discovery of business interfaces without burdening stakeholders with excessive details. Through cataloging APIs and their dependencies, organizations can successfully manage the maturity of their systems and gain a comprehensive understanding of ownership. This comprehensive approach empowers EAM teams to make informed decisions, optimize workflows, and achieve successful outcomes.
Empower your development teams to take technology decisions with context and guidance
Only a few experts could tell me what was really running in our Kubernetes clusters and in Azure. - Steffen Wittmann, CTO@LeanIX
Organizations face a critical challenge in empowering their development teams to make informed technology decisions with context and guidance. Without this empowerment, teams struggle to keep pace with emerging technologies, resulting in inefficiencies, missed innovation opportunities, and a disengaged workforce. Lack of empowerment leads to disconnection from decision-making processes, making it difficult for teams to align their work with strategic goals and market needs. Moreover, without the necessary context and guidance, teams struggle to assess suitable technologies, leading to poor choices and wasted resources. At LeanIX we believe that empowering development teams is crucial to drive innovation, adapt to market demands, and foster a culture of ownership and creativity within the organization.
Automated discovery of your tech stack
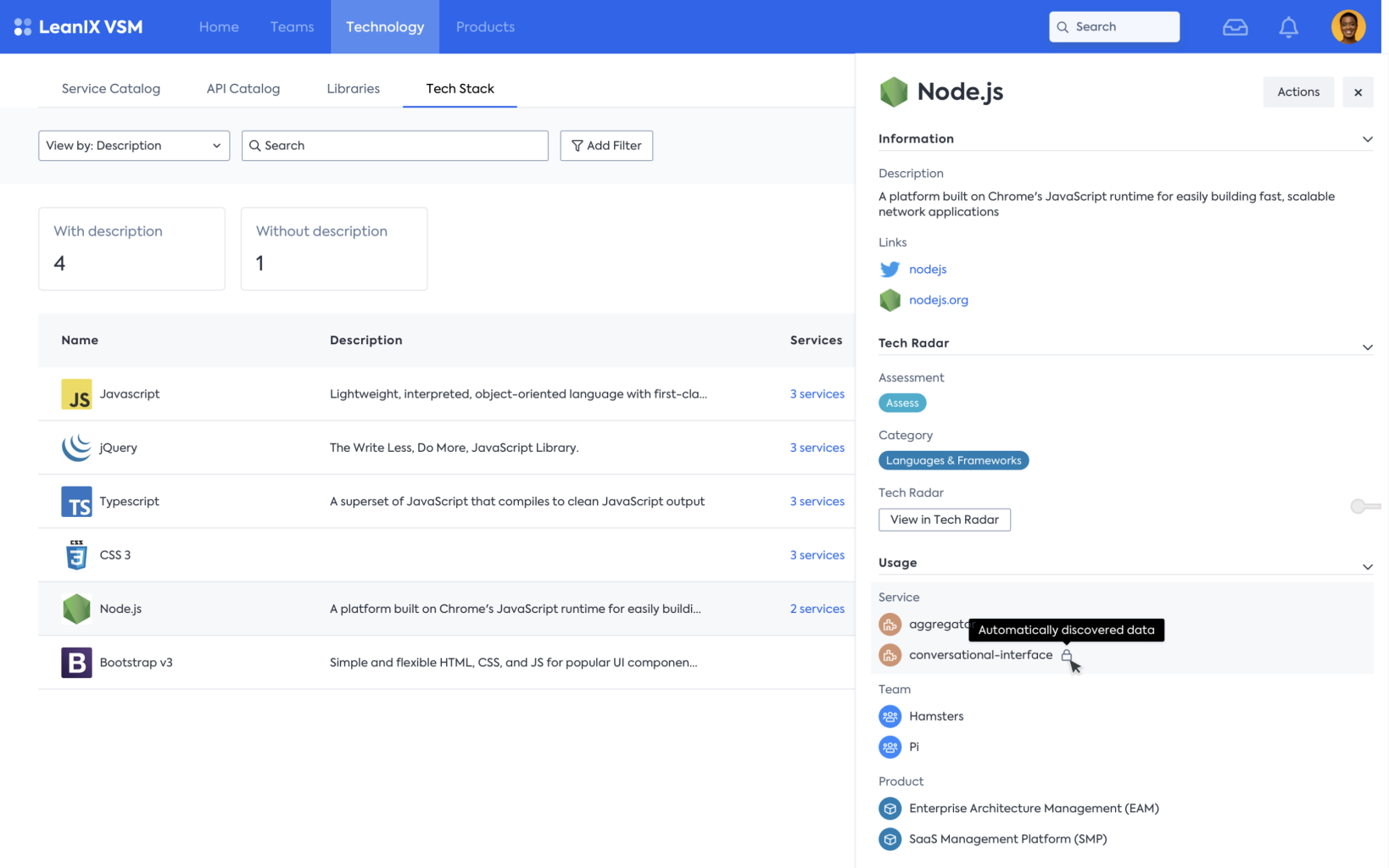
Automated discovery of the tech stack combined with manual additions enables organizations to efficiently and accurately identify the technologies and components comprising their infrastructure. By leveraging the public cloud(e.g. Azure or AWS), Kubernetes (k8s), and code composition analysis, companies can comprehensively discover their tech stack, including both cloud-based and on-premises systems. Contextualizing the data obtained through this discovery process with information about services, teams, and products provides a holistic understanding of the organization's technological landscape, facilitating effective decision-making, resource allocation, and strategic planning.
Use the Tech Radar to communicate tech stack strategy to your organization
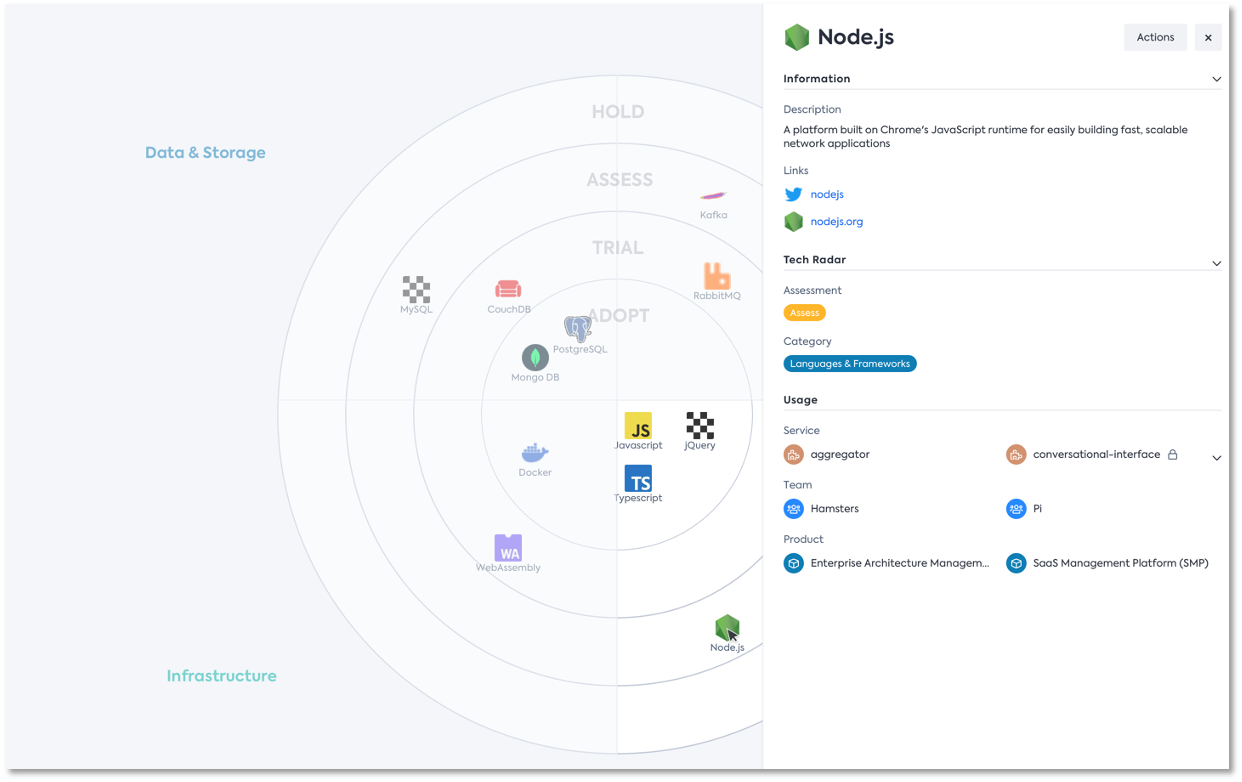 To effectively communicate the tech stack strategy to the organization, the Tech Radar can be employed as a valuable tool. The Tech Radar visually presents the company's technology decisions, guiding teams by providing clear and efficient communication channels. By leveraging information about the current usage and composition of technologies within the organization, the Tech Radar can be continually evolved and updated, ensuring that it remains a relevant and practical resource for decision-making and aligning the tech stack with the company's evolving needs and goals.
To effectively communicate the tech stack strategy to the organization, the Tech Radar can be employed as a valuable tool. The Tech Radar visually presents the company's technology decisions, guiding teams by providing clear and efficient communication channels. By leveraging information about the current usage and composition of technologies within the organization, the Tech Radar can be continually evolved and updated, ensuring that it remains a relevant and practical resource for decision-making and aligning the tech stack with the company's evolving needs and goals.
VSM's tech stack also informs your digital transformation journey
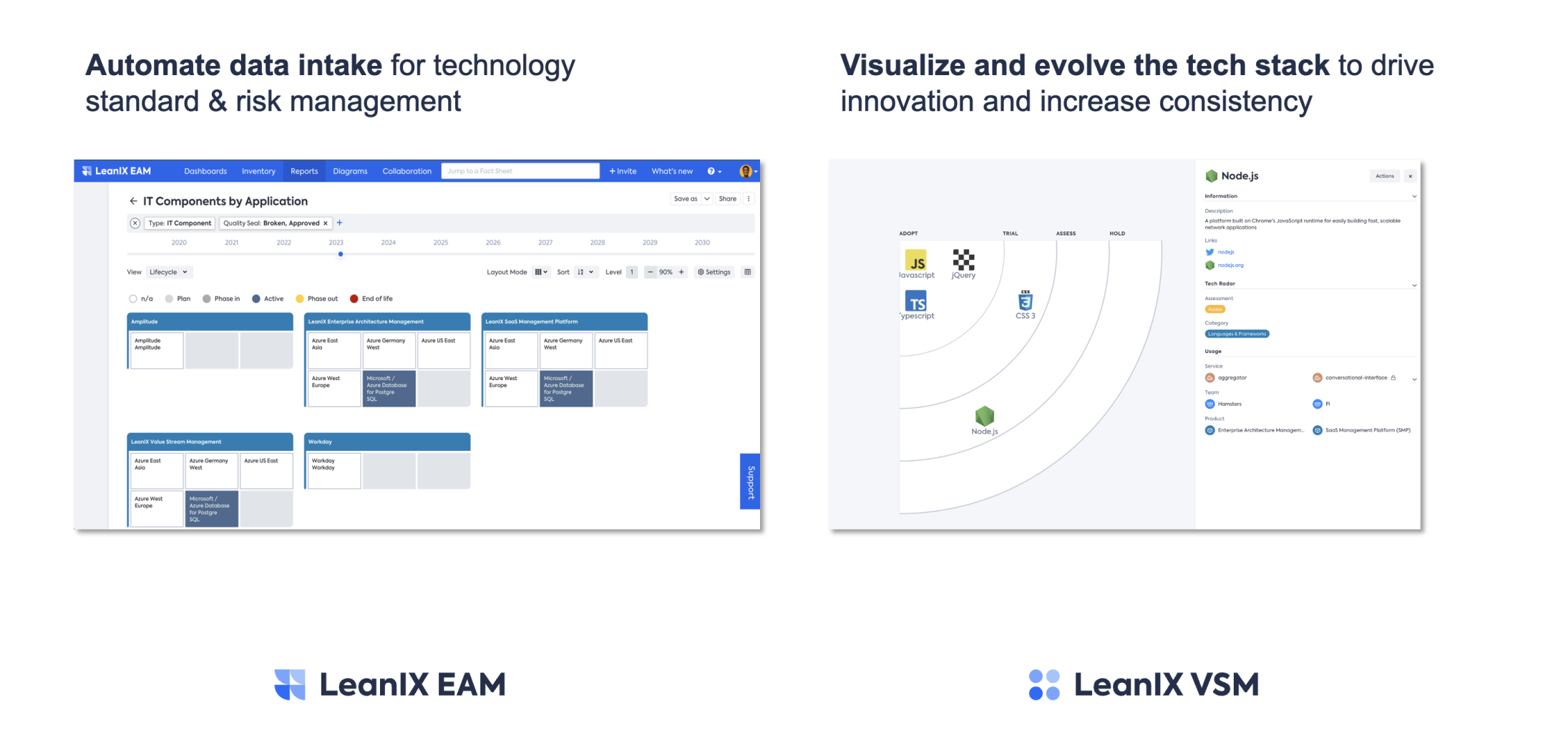 The tech stack serves as a valuable resource in informing the digital transformation journey of Enterprise Architects. By visualizing and continuously evolving the tech stack, Enterprise Architects can drive innovation and increase consistency throughout the organization. Furthermore, automating data intake for technology standards and risk management enables efficient monitoring and governance of the tech stack, ensuring compliance with standards and mitigating potential risks in a proactive manner.
The tech stack serves as a valuable resource in informing the digital transformation journey of Enterprise Architects. By visualizing and continuously evolving the tech stack, Enterprise Architects can drive innovation and increase consistency throughout the organization. Furthermore, automating data intake for technology standards and risk management enables efficient monitoring and governance of the tech stack, ensuring compliance with standards and mitigating potential risks in a proactive manner.
Visit our roadmap and try VSM for free
If you want to find out more about what we have planned for LeanIX VSM check out our public roadmap at roadmap.leanix.net. You can also try the latest version of our product in a free trial.
Updated 9 months ago
